Team Building one hundred and one
Content
Prepare your group for every stage, and use instruments like Lucidchart to stipulate their roles and obligations throughout the journey. Keeping visual pointers what are the 4 stages of group development throughout the method is vital for sustaining the integrity of your staff and avoiding conflict and confusion.
Keeping these levels in thoughts, a lot of the issues that I see with teams are ones of battle where groups get stuck within the Storming stage. Conflicts are regularly flaring up as a result of people usually do not https://globalcloudteam.com/four-stages-of-team-development-what-you-need-to-know/ have the talents and/or maturity to effectively handle their variations. These differences are both perpetual open sores or they’re swept underneath the carpet solely to fester and rear their ugly heads on the most disastrous times.
SCT also emphasizes the need to acknowledge the phases of group development and the defenses associated to each part so as to greatest make sense and influence group dynamics. They use suggestions, drawback fixing, and function play to achieve insights into themselves, others, and teams.
Keep the levels of staff improvement in thoughts as you guide your team from Forming to Performing. Unfortunately the Performing stage just isn’t a guaranteed facet of your season.
As Bruce mentions, these levels may be cyclical as soon as changes occur, such because the introduction of a brand new group member or the change of another group variable that can modify how the team works. I particularly see these phases applicable in direction of Enterprise 2.zero initiatives where many firms are introducing new groups and methods to help https://globalcloudteam.com/ make the initiatives worthwhile. Hopefully, the stages of group growth will provide greater perception into the inevitable levels you will encounter when a new team comes together. Through understanding and persistence, leaders can effectively navigate and cut back the time spent within the earlier phases, guiding a group toward Performing extra rapidly.
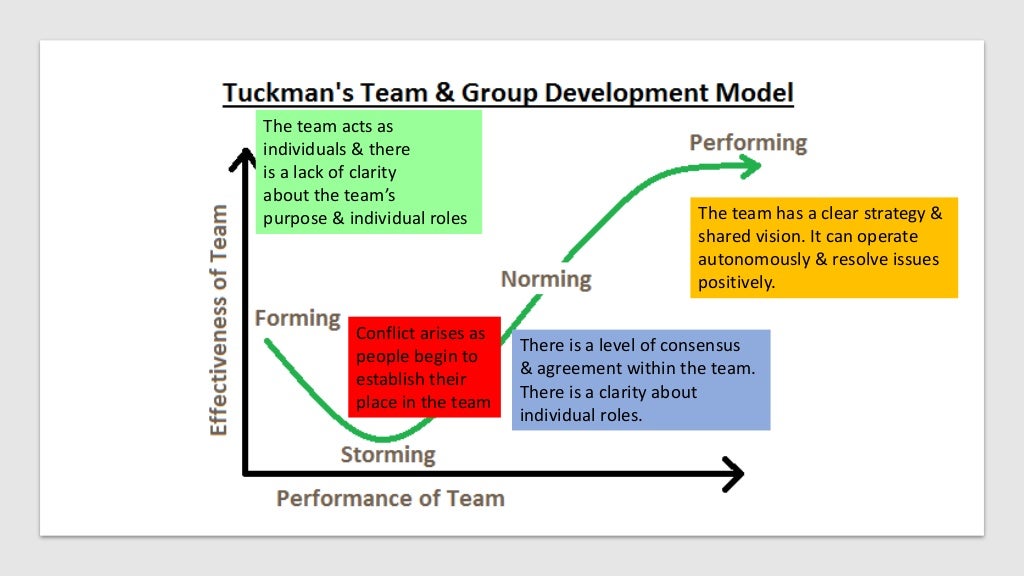
The norms which might be established may be totally counterproductive to your team’s success. For instance, “Do just enough to get by,” “Every person for themselves,” “Coach plays favorites,” are all norms and attitudes which have prevented groups from reaching their potential. Teams with poor standards regularly maintain themselves from progressing. This stage follows Norming and occurs solely after efficient standards are in place and firmly embraced by the staff. The team begins performing as a cohesive unit that respects and trusts each other.
Teams can travel between these phases, particularly as new challenges and calls for arise in the course what is devsecops of the season. Injuries, conflicts and losses could cause a staff to regress from the Norming stage back into the Storming stage.
Some observers caution that the group growth process isn’t as clear-minimize and linear as Tuckman describes. Groups could cycle forwards and backwards between different stages, and at times, group conduct could not clearly match the mannequin. However, models aren’t supposed to precisely replicate what occurs in the true world. Instead, they provide a common illustration of real-world events. Tuckman’s 5-stage group improvement model still provides important insights into the small group development course of.
Allow Your Team To Learn From Home
Performing requires that your staff has constructively dealt with the conflict of the Storming stage. The Norming stage occurs when your group begins to choose a algorithm and standards as to how issues shall be accomplished. Norming relates to your staff’s requirements in practices, the classroom, weight coaching, conditioning, psychological training, social life, and so forth. As a coach, it is important that the group norms you determine assist to create and foster a profitable surroundings.
What is the working stage of a group?
Stages of Group Development: Forming, Storming, Norming, Performing & Adjourning.
The levels of group growth in organizational habits and administration are a concept of team improvement — a gaggle-forming model that consists of 5 distinct phases. During this stage, the team has resolved most of its conflicts and grown closer. There is settlement on a standard objective and group members have, for essentially the most part, rallied round leadership. This newfound unity usually extends exterior of the workplace as members begin to socialize in off-hours. It’s one factor to be given a task and fairly one other to get a gaggle to successfully complete that task.
- To help a gaggle at the forming stage, a leader ought to present clear directions and explain goals to keep away from exaggerated expectations.
- The knowledge of those levels matters as a result of they help leaders to know what their subordinates experience as group members and the way they will foster the further growth of their teams.
- When you understand it, you can help your new team become efficient more quickly.
- Bruce Tuckman’s Forming, Storming, Norming, and Performing mannequin describes these stages.
- Forming a group takes time, and members usually go through recognizable levels as they change from being a collection of strangers to a united group with frequent targets.
- The role of a group chief is to define the current stage of the team formation and answer the questions that sometimes come up at this part.
Sometimes your group may revert again to behavior from the storming stage. Sometimes there’s overlap between the storming and norming stage. And sometimes the storming stage seems to last for much longer than is critical. Keep to the project’s timeline and keep referring to the organizational tools you’ve developed.
Why Are The Stages Of Group Development Important?
Remember that every participant enters the season with a sure set of expectations of how things should be for them individually and for the remainder of the group. Naturally battle arises when the expectations and desires of assorted individuals forming storming norming come into contact. Once a group is clear about its wants, it could possibly transfer ahead to the third stage of group growth, the norming stage. The first stage of group growth is the forming stage.
Coach staff members in assertiveness and conflict resolution expertise, where this is essential. Later, he added a fifth stage, “adjourning” (which is sometimes generally known as “mourning”). The question that individuals ask during the norming stage of group growth is, “What do the others anticipate me to do? ” It issues as a result of the data of questions that team members ask themselves at different stages of staff development helps a pacesetter to handle them effectively.
Why do teams not go to Stage 4?
Explanation In the storming stage, team members open up with their competing ideas about how the team should approach work. This stage is typically the least productive, since team members are attempting to make sense of uncertain roles, goals, and accountabilities.
Better Organize Your Day With This Time Management Technique
This stage presents a time the place the group is just beginning to come together and is described with anxiety and uncertainty. As the team strikes out of the Storming part they will enter the Norming section. This tends to be a move in the direction of harmonious working practices with teams agreeing on the principles and values by which they function.

The objective of Bruce Tuckman’s Stages model was to help project leaders perceive how their staff members had been constructing relationships together. As it seems, people strategy duties differently depending on the standard of their relationships with their co-staff. As you notice, you are an essential catalyst in monitoring and mixing your team’s chemistry.
Then, use this knowledge to help you overcome problems and reach your project targets with success. Clarify the anticipated stages of group growth proper from the beginning, to spotlight that conflicts and issues throughout the project are regular, and never an indication of failure.
Recognize The Value Of Each Team Member.
In 1965, Dr. Bruce Tuckman printed the Tuckman model, in which he detailed the stages of staff growth. Whether you are a manager or are merely one of the group what is mysql, once you perceive these phases of group development, you can assist your group push past challenges and become a high-performing unit.
